Google has confirmed a Salesforce CRM breach that exposed millions of records linked to Google Ads customers and potential clients.
Quick Summary – TLDR:
- Hackers accessed a Google corporate Salesforce instance, stealing contact data for up to 2.55 million Google Ads customers.
- Threat groups ShinyHunters and Scattered Spider, now calling themselves Sp1d3rHunters, claimed responsibility.
- Attackers used advanced social engineering and malicious Salesforce Data Loader tools to exfiltrate data.
- Google says no payment or Ads account data was compromised, but phishing and extortion risks remain high.
What Happened?
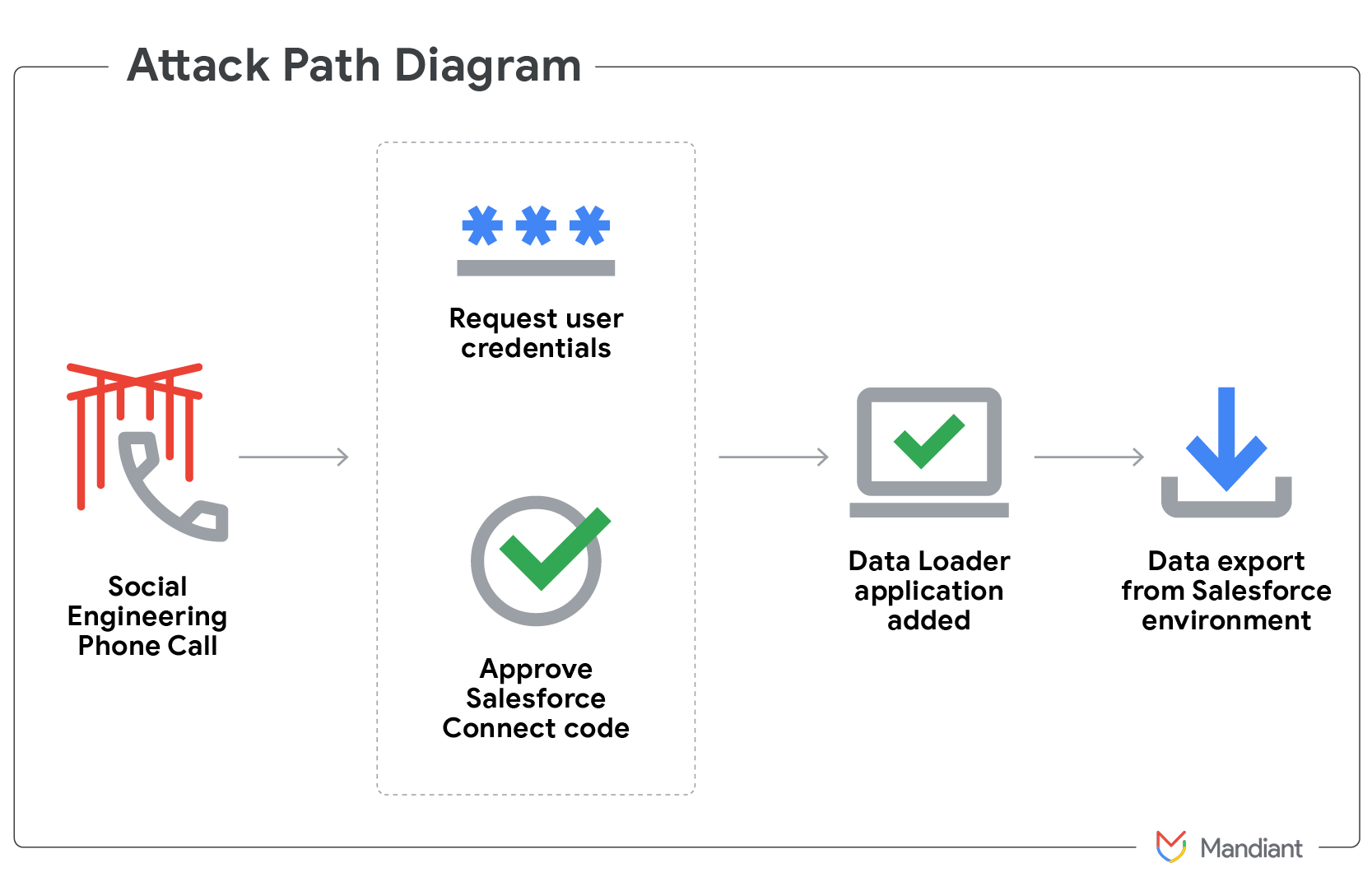
Google confirmed a data breach involving one of its Salesforce CRM instances, impacting customer and prospect contact data for its Google Ads platform. The incident, which was detected in June 2025, came to public attention in early August after the company began notifying affected customers. While the stolen information included business names, phone numbers, email addresses, and related sales notes, Google emphasized that no payment data or Ads account details were compromised.
Breach Linked to ShinyHunters and Scattered Spider
The attack was carried out by ShinyHunters, a well-known cybercrime group, in collaboration with members of Scattered Spider. Together, they now operate under the name Sp1d3rHunters. The group claims it stole around 2.55 million records, though it is unclear if duplicates are included.
Google’s Threat Intelligence Group (GTIG) revealed that the breach was achieved through sophisticated voice phishing (vishing) and other social engineering tactics. Employees were tricked into authorizing a malicious connected app, a modified version of Salesforce’s Data Loader, granting attackers full database access.
The Ransom Demand and Hacker Claims
Following the breach, ShinyHunters allegedly demanded 20 Bitcoins (approximately $2.3 million) from Google to avoid leaking the stolen data. However, the group later claimed the ransom was sent as a joke, stating it was “for the lulz.” Despite this claim, GTIG warns that extortion attempts could follow, as hackers often monetize stolen data months after the theft.
New Hacking Tools and Growing Threat
ShinyHunters admitted to upgrading their tools, moving from Salesforce’s Data Loader to custom Python scripts. These scripts are faster and less detectable, allowing for more efficient data theft from compromised Salesforce environments. The attackers also used Mullvad VPN and TOR to mask their identities.
GTIG has observed infrastructure overlaps between Sp1d3rHunters and other cybercrime collectives like “The Com,” which have targeted major cloud platforms including Okta and Microsoft 365.
Google’s Response and Security Recommendations
Google acted quickly after detecting the intrusion, revoking unauthorized access and securing the affected Salesforce instance. The company stressed that this was a social engineering breach, not a flaw in Salesforce’s own platform.
GTIG recommends several measures to prevent similar attacks:
- Restrict API Enabled permissions and enforce least privilege access.
- Implement allowlisting for connected apps and limit permissions to trusted administrators.
- Set IP restrictions to block unauthorized VPN or TOR logins.
- Use Salesforce Shield for real-time event monitoring and transaction security.
- Enforce multi-factor authentication (MFA) and train staff to spot phishing attempts.
SQ Magazine Takeaway
Honestly, this is another wake-up call about how social engineering remains one of the most dangerous attack methods. It is not just about firewalls and encryption. One well-crafted phone call or fake app can undo millions in security investment. The fact that these hackers are now refining their tools for quicker and stealthier attacks means the next big breach might already be in progress somewhere else. If you use Salesforce or store valuable customer data, now is the time to tighten access controls and train your team. Prevention is still cheaper than ransom.


































































