In March 2025, a small logistics company in Ohio lost access to every operational file it had overnight. Trucks sat idle, routes scrambled, and customer data vanished into encryption. The attackers demanded payment in Bitcoin, $210,000, to unlock the systems. The company paid. What happened next? The decryptor didn’t work. And the company ended up paying again, for new systems, legal support, and crisis PR.
This isn’t an isolated story. It’s a snapshot of how ransomware continues to evolve: from a criminal novelty into a predictable, profitable industry. In this article, we’ll break down the numbers behind ransomware in 2025, from global trends and attack vectors to industry impacts and regional vulnerabilities, so you can understand how the threat has matured and what to expect next.
Editor’s Choice
- 68% of ransomware victims in 2025 experienced a second attack within six months of the first.
- The average ransom demand in 2025 has risen to $1.52 million.
- 41% of successful attacks in 2025 were linked to exploited zero-day vulnerabilities, doubling the rate from two years ago.
- In 2025, 47% of ransomware payloads are now deployed via compromised third-party software, particularly MSPs.
- The healthcare sector saw the highest number of attacks in Q1 2025, accounting for 26% of all reported cases globally.
- 33% of ransomware payments in 2025 are made in Monero (XMR), overtaking Bitcoin for the first time in anonymized transactions.
- The average downtime following an attack in 2025 is 24.6 days.
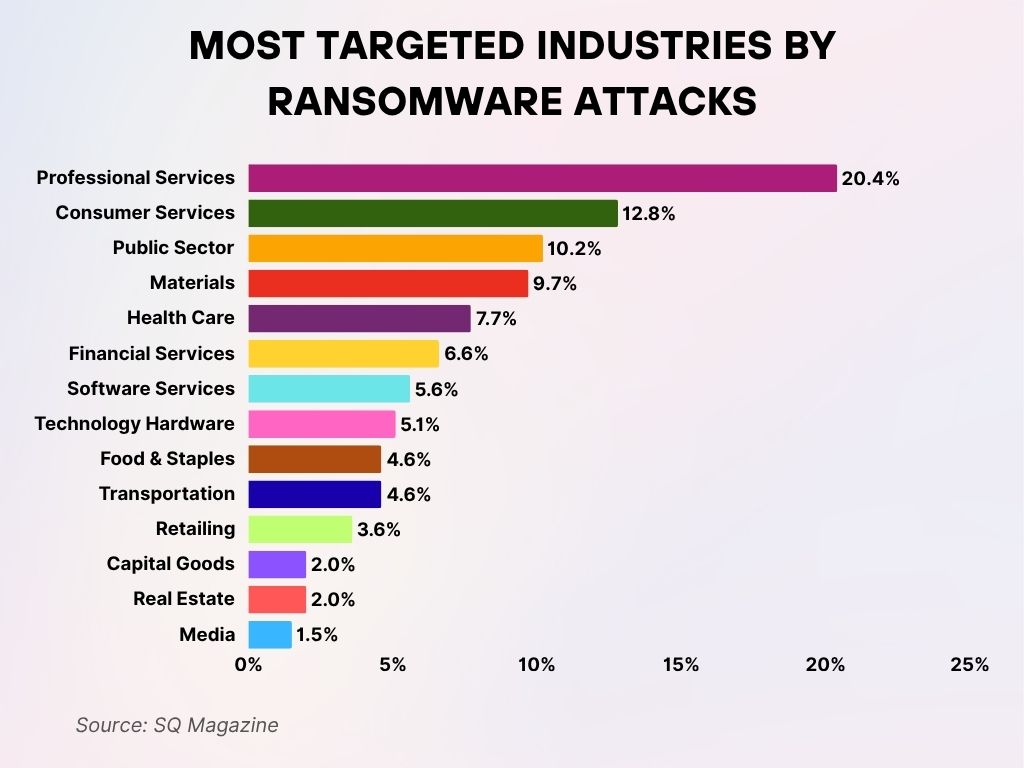
Most Targeted Industries by Ransomware Attacks
- Professional Services face the highest share of ransomware attacks, accounting for 20.4% of all incidents.
- Consumer Services rank second, targeted in 12.8% of cases.
- The Public Sector is also heavily hit, with 10.2% of attacks directed at government and public institutions.
- Materials industries follow closely behind, experiencing 9.7% of ransomware threats.
- The Health Care sector, a critical infrastructure, is targeted in 7.7% of attacks.
- Financial Services experience 6.6% of ransomware incidents, showing the growing risk in this data-sensitive field.
- Software Services represent 5.6% of attacks, highlighting risks in the tech development space.
- Technology Hardware companies are affected in 5.1% of cases.
- Food & Staples and Transportation are each targeted in 4.6% of attacks, showing vulnerabilities in essential goods and logistics.
- Retailing sees 3.6% of attacks, indicating exposure in consumer-facing sectors.
- Both Capital Goods and Real Estate sectors report 2.0% of ransomware incidents.
- Media organizations are the least targeted, making up only 1.5% of reported cases.
Average Ransom Demands and Payouts
- The average ransom demand in 2025 is $1.52 million.
- The median ransom paid by victims in 2025 is $408,000, due to better negotiation practices.
- The highest confirmed payout in 2025 so far is $12.4 million, paid by a global logistics conglomerate.
- 45% of companies in 2025 still choose to negotiate before paying, often reducing demands by up to 30%.
- 41% of firms pay some form of ransom in 2025, down from 46% last year, reflecting improved backup strategies.
- Ransomware groups offering “data deletion guarantees” for higher-tier payments now appear in 23% of negotiations in 2025.
- Crypto tracing success rates have improved in 2025, with law enforcement now able to track 36% of ransom flows within 48 hours.
- 30% of ransom demands in 2025 include tiered pricing, charging more if victims delay payment past a 5-day window.
- Insider-assisted ransom attacks have been involved in 6% of confirmed payouts so far in 2025, a new operational wrinkle.
- Ransomware actors now issue “performance-based” demands, e.g., higher ransom if endpoint detection tools delayed payloads, seen in 11% of cases in 2025.
Frequency of Ransomware Attacks by Region
- North America leads with 41% of global ransomware incidents in 2025.
- Europe comes second with 28%, with significant activity in Germany, France, and the UK.
- Asia-Pacific holds 17% of global attack volume in 2025, up from 13% last year, largely due to increased cloud exploitation.
- Latin America has seen 8% of ransomware activity in 2025, with Brazil and Mexico as primary targets.
- Middle East and Africa represent a combined 6% of attacks in 2025, often underreported due to limited cyber response infrastructure.
- Australia and New Zealand combined account for 3.4% of ransomware reports in 2025.
- Russia and Eastern Europe show the lowest attack frequency, with under 1.5% of global cases, often considered “safe zones” by some ransomware gangs.
- Cross-border attacks in 2025 have grown by 19%, with threat actors targeting globally distributed cloud networks.
- Multinational organizations experienced ransomware incidents in an average of 3.2 regions simultaneously during 2025 breaches.
- Localized ransomware variants, tailored by region and language, now account for 22% of attacks as of mid-2025.
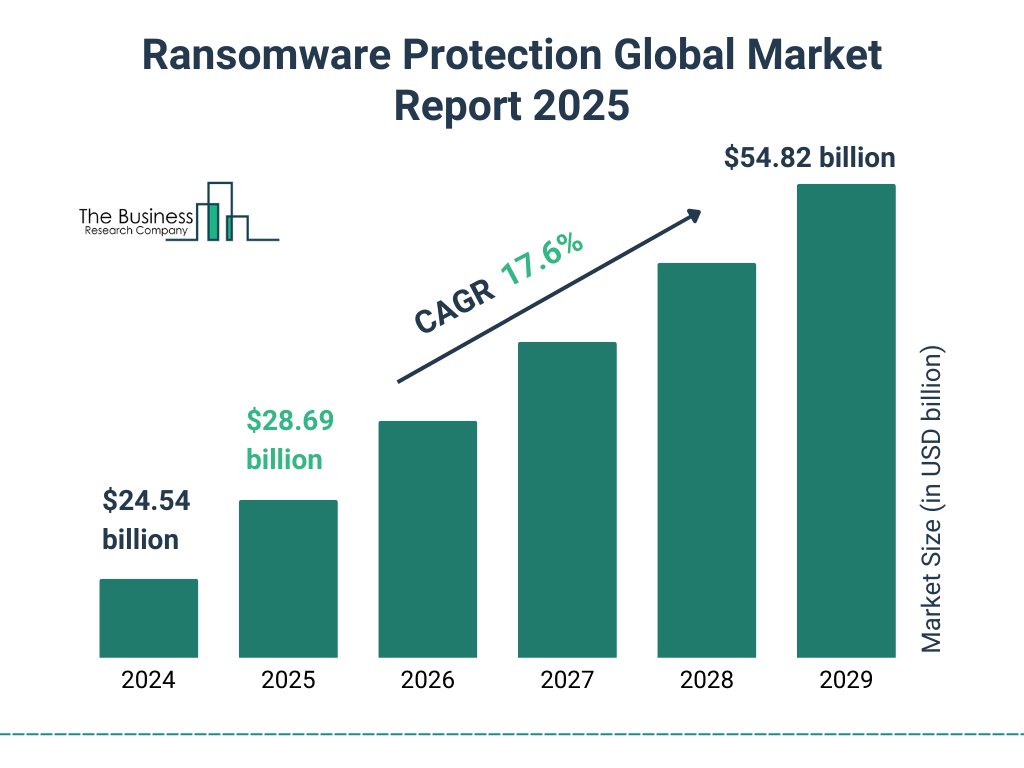
Ransomware Protection Global Market Growth Forecast
- The global ransomware protection market is projected to reach $28.69 billion in 2025.
- By 2029, the market is forecast to hit $54.82 billion, more than doubling its size from 2024.
This surge reflects the increasing urgency among businesses and governments to invest in cybersecurity solutions.
Impact of Ransomware on Small vs. Large Businesses
- In 2025, 78% of ransomware victims are small to midsize businesses (SMBs).
- Large enterprises still account for 22% of attacks, but they experience 74% higher average downtime costs than SMBs.
- The average ransom demand for large companies in 2025 is $2.9 million, compared to $486,000 for SMBs.
- SMBs in 2025 report a 60% lower cybersecurity investment per endpoint, making them easier targets for automated attacks.
- 51% of SMBs that suffered an attack in 2025 were offline for more than 10 days.
- 38% of affected large businesses in 2025 experienced operational disruption across multiple departments, amplifying loss.
- Human-operated ransomware targets large firms more frequently, accounting for 69% of breaches in enterprise environments.
- In 2025, 40% of SMBs impacted by ransomware reported laying off staff within three months of the incident.
- 87% of SMBs lack a dedicated incident response plan in 2025.
- Cyber insurance premiums for SMBs increased by an average of 24% in 2025, largely due to persistent ransomware risks.
Common Ransomware Attack Vectors
- Phishing emails remain the most prevalent attack vector, accounting for 42% of ransomware breaches in 2025.
- Compromised remote access tools were used in 28% of attacks in 2025, particularly via exposed RDP and VPN services.
- Software supply chain exploits were responsible for 16% of ransomware deployments in 2025, often via third-party libraries.
- Misconfigured cloud environments led to 7% of ransomware intrusions in 2025, a rising concern as multicloud adoption grows.
- Drive-by downloads, often from malicious ads, account for 3.5% of initial ransomware infections in 2025.
- QR code phishing is an emerging tactic in 2025, used in 1.6% of ransomware campaigns, targeting mobile-first users.
- Deepfake-enabled social engineering has led to 2.1% of ransomware cases in 2025.
- Compromised credentials from dark web marketplaces were linked to 23% of initial access in ransomware attacks in 2025.
- Exploiting outdated VPN firmware contributed to 11% of confirmed attacks in 2025.
- USB-based ransomware payloads, though rare, have appeared in 0.8% of attacks in 2025, primarily in offline environments.
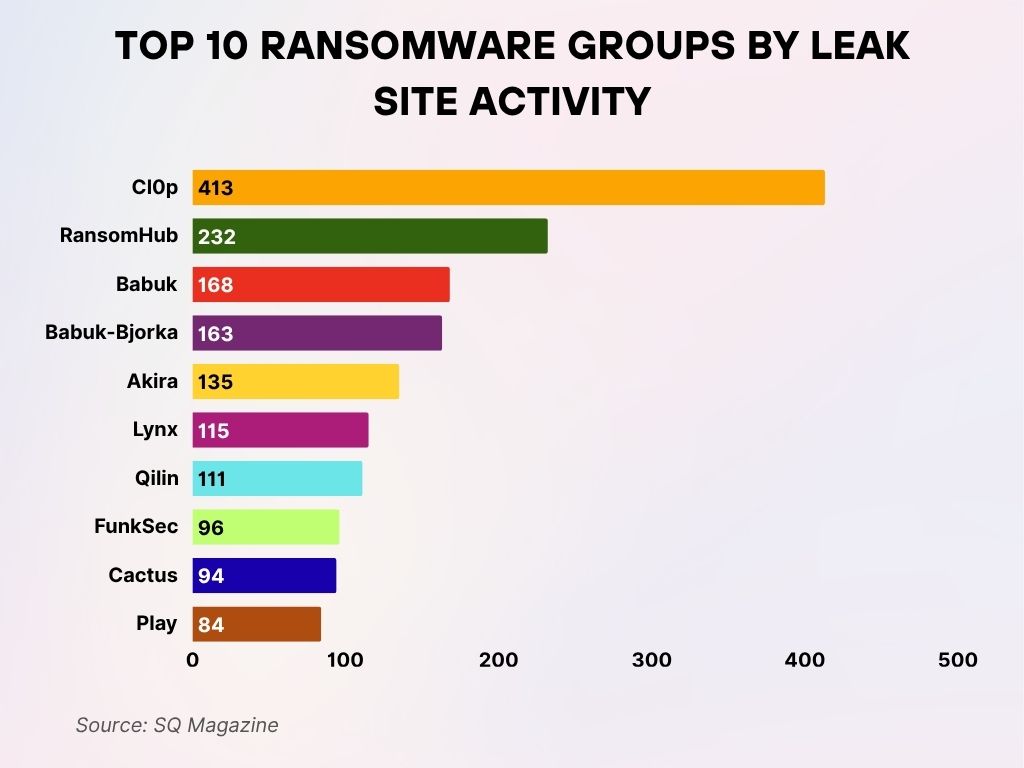
Top 10 Ransomware Groups by Leak Site Activity
- Cl0p leads all ransomware groups with 413 leak site posts, dominating Q1 2025 activity.
- RansomHub ranks second, responsible for 232 posts, showing consistent aggressive tactics.
- Babuk posted 168 times, while its variant Babuk-Bjorka followed closely with 163 posts.
- Akira registered 135 leak site posts, continuing its growth in cyberattack campaigns.
- Lynx contributed 115 posts, placing it mid-tier among top ransomware threats.
- Qilin accounted for 111 posts, maintaining a significant online presence.
- FunkSec made 96 posts, signaling a rising threat in the ecosystem.
- Cactus followed with 94 posts, just slightly behind FunkSec.
- Play rounds out the top 10 with 84 posts during the quarter.
Rise of Ransomware-as-a-Service (RaaS)
- In 2025, 72% of ransomware incidents are attributed to Ransomware-as-a-Service (RaaS) operations.
- The top 5 RaaS groups are responsible for 58% of all observed ransomware payloads in the first half of 2025.
- The average RaaS affiliate earns $21,000 per successful infection in 2025, based on shared revenue models.
- New RaaS listings on darknet markets increased by 36% in the first quarter of 2025.
- RaaS subscription costs range from $250 to $1,200/month in 2025, depending on payload capabilities.
- 45% of RaaS payloads now include “evade EDR” modules in 2025.
- RaaS platforms in 2025 advertise customer support, offering “guaranteed file decryption” for paid victims.
- Telegram remains the most used communication tool for RaaS operators, involved in 62% of threat actor channels in 2025.
- 38% of all new ransomware strains** in 2025 are derivatives of RaaS kits, customized by affiliates.
- RaaS marketplaces now offer bundled services, including access brokers, phishing kits, and crypters, for as low as $500 in 2025.
Role of Cryptocurrency in Ransom Payments
- In 2025, Monero (XMR) surpassed Bitcoin, making up 33% of total ransom payments due to improved anonymity.
- Bitcoin (BTC) still accounts for 28% of payments in 2025, favored for liquidity despite traceability risks.
- Tether (USDT) now comprises 19% of payments in 2025, especially in Asia and Eastern Europe, due to stability.
- Ethereum (ETH) and other altcoins account for the remaining 20%, often used for splitting or laundering transactions.
- Ransomware gangs in 2025 use mixing services for 77% of transactions, with a growing reliance on decentralized exchanges (DEXs).
- The average crypto laundering cycle has shortened to 3.4 days in 2025.
- Blockchain analytics firms in 2025 have helped authorities recover an estimated $84 million in ransom payments so far.
- Double extortion models often require payment in two currencies, e.g., Monero for file decryption and Bitcoin for data deletion, in 11% of cases.
- Crypto tracing is now built into law enforcement playbooks in 18 major countries as of 2025.
- Over 140 crypto wallets linked to ransomware groups have been sanctioned or blacklisted by global agencies in 2025.
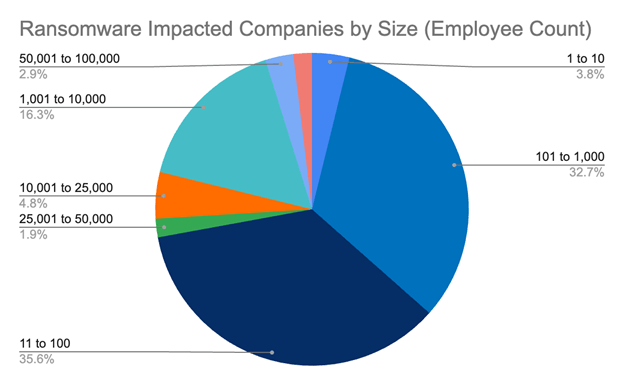
Ransomware Impact by Company Size (Employee Count)
- The majority of impacted companies have 11 to 100 employees, making up 35.6% of cases.
- Businesses with 101 to 1,000 employees are close behind, accounting for 32.7% of ransomware victims.
- 16.3% of affected companies fall within the 1,001 to 10,000 employee range.
- Only 4.8% of attacks target companies with 10,001 to 25,000 employees.
- Very small businesses with 1 to 10 employees still represent 3.8% of incidents.
- 2.9% of ransomware-hit organizations have 50,001 to 100,000 employees.
- Enterprises with 25,001 to 50,000 employees make up just 1.9% of the total.
Ransomware Recovery Time and Downtime Costs
- The average recovery time from a ransomware attack in 2025 is 24.6 days.
- Downtime costs average $356,000 per day for mid-market companies in 2025, not including ransom or legal fees.
- 37% of companies hit by ransomware in 2025 experienced partial data loss despite paying.
- Full restoration without backups took an average of 16.8 days in 2025, depending on the ransomware strain.
- 79% of affected organizations used third-party incident response firms in 2025 to facilitate recovery.
- The average cost of full recovery, including legal, technical, and operational efforts, is $1.68 million in 2025.
- Cloud-first companies recovered 35% faster than those reliant on hybrid infrastructure in 2025.
- Businesses with immutable backups in place experienced 90% lower recovery times than those without.
- Ransomware “re-infection” rate within 90 days of recovery is 9.4% in 2025.
- Insurance-covered firms report that 57% of recovery expenses were reimbursed within 60 days of claim submission in 2025.
Percentage of Organizations Paying the Ransom
- In 2025, 41% of ransomware victims chose to pay the ransom.
- 59% of victims refused to pay, citing data backup confidence, legal risks, or ethical concerns.
- Among those who paid, only 67% successfully regained full access to their data in 2025.
- 21% of paying organizations were extorted a second time within 45 days, often by a different affiliate group.
- Publicly traded companies are less likely to pay, with only 24% admitting to payment in 2025, down from 32%.
- Legal mandates in jurisdictions like the EU and Australia discourage ransom payment, and reporting is now mandatory for 85% of cases.
- Cyber insurance now covers ransom payments for only 48% of policyholders in 2025.
- Organizations with incident response teams in place were 72% less likely to pay the ransom in 2025.
- Ransom payments over $1 million were reported in 19% of paying cases in 2025.
- Law enforcement guidance influenced the decision not to pay in 35% of cases reported so far in 2025.
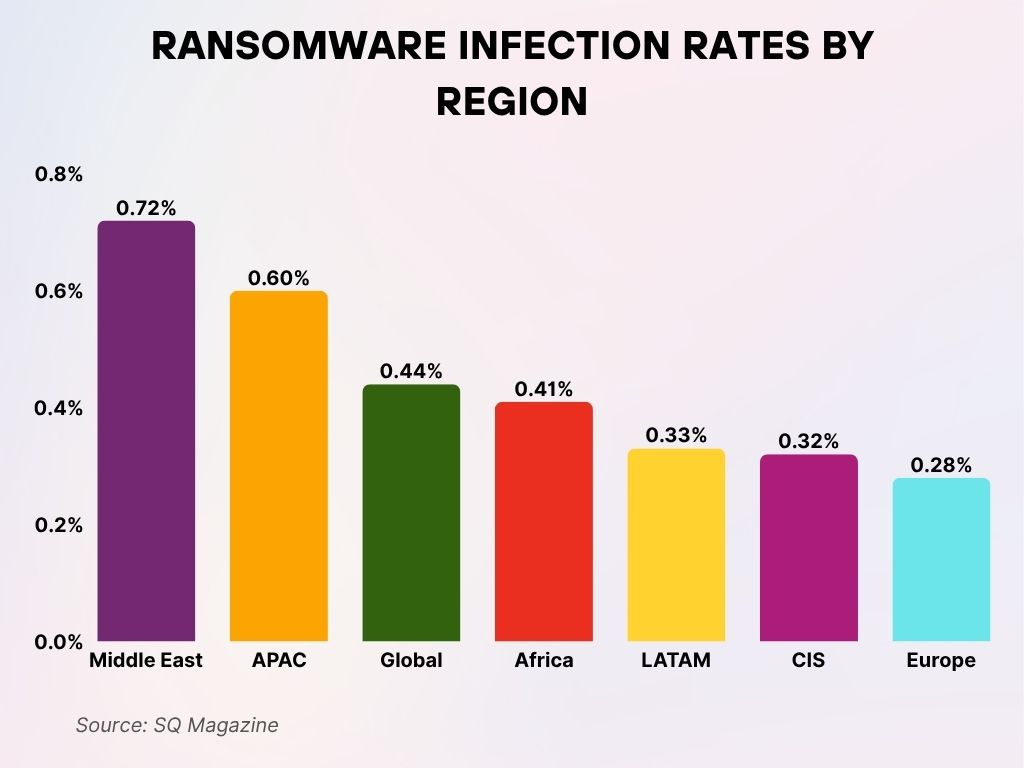
Ransomware Infection Rates by Region
- The Middle East has the highest ransomware infection rate at 0.72%, leading all global regions.
- APAC (Asia-Pacific) follows closely with an infection rate of 0.60%.
- The Global average stands at 0.44%, serving as a benchmark for regional comparisons.
- Africa reports a slightly lower rate of 0.41%, just under the global average.
- LATAM (Latin America) experiences an infection rate of 0.33%.
- The CIS region (Commonwealth of Independent States) is nearly on par, with a rate of 0.32%.
- Europe has the lowest infection rate, recorded at 0.28%.
Law Enforcement and Government Response
- In 2025, 22 countries have formally criminalized ransom payments to designated threat actors.
- The FBI’s IC3 division received over 161,000 ransomware-related complaints in the first half of 2025, up 47% year-over-year.
- Europol assisted in 13 coordinated takedowns of ransomware networks in 2025.
- The US Treasury blocked over $135 million in suspicious crypto transactions linked to ransomware wallets as of May 2025.
- Interpol’s Global Cybercrime Centre identified 19 new ransomware groups operating across national borders this year.
- Cyber Command operations disrupted 8 active ransomware campaigns in Q1 and Q2 of 2025, most of them RaaS operations.
- The Cybersecurity and Infrastructure Security Agency (CISA) in the US launched 25 regional threat intel hubs in 2025 to combat ransomware spread.
- Public-private partnerships are active in 33 countries as of 2025, aimed at creating real-time alert systems for active threats.
- In 2025, over 600 arrests were made globally tied directly to ransomware infrastructure or proceeds.
- New legislation in 7 US states now mandates the disclosure of ransomware attacks within 48 hours, with penalties for non-compliance.
Notable Ransomware Attacks Reported
- In February 2025, a ransomware attack shut down Los Angeles’ Metro rail control systems for 18 hours, delaying over 400,000 commuters.
- April 2025 saw a ransomware campaign against 10 major hospital systems across the Midwest, affecting over 2 million patients’ records.
- A Fortune 500 law firm paid a ransom of $7.6 million in March 2025 after client case files were locked and partially leaked.
- A university consortium in the northeastern US faced an attack in January 2025, halting operations at six campuses for nearly one week.
- In May 2025, a ransomware variant dubbed “ShutterLock” infected CCTV and surveillance systems in 8 US airports, causing major delays.
- The largest ransomware payout reported in 2025 so far is $12.4 million, by a logistics conglomerate in Singapore.
- A Canadian cloud hosting firm went offline for six days in 2025, disrupting over 9,000 client websites, including several healthcare portals.
- A new group, PhantomLoop, claimed responsibility for three global hotel chain breaches in early 2025, leaking customer data from over 10 million reservations.
- Educational institutions reported over 2,300 ransomware incidents by mid-2025, with most attacks occurring around final exam periods.
- The first AI-aided ransomware campaign, confirmed in 2025, generated unique payloads in real-time based on endpoint configurations.
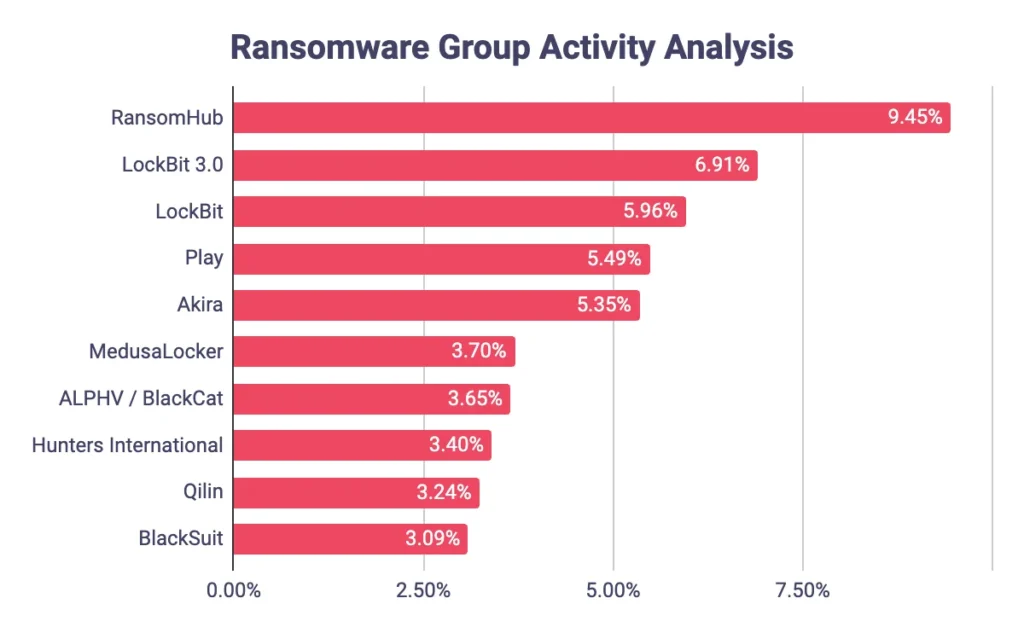
Ransomware Group Activity Breakdown
- RansomHub is currently the most active ransomware group, responsible for 9.45% of all known attacks.
- LockBit 3.0 follows with a strong presence, accounting for 6.91% of activity.
- The earlier version, LockBit, still contributes 5.96% to the global ransomware footprint.
- Play group is behind 5.49% of attacks, showing persistent visibility in the threat landscape.
- Akira contributes 5.35%, maintaining its position among top-tier ransomware actors.
- MedusaLocker is responsible for 3.70% of observed ransomware incidents.
- ALPHV / BlackCat accounts for 3.65% of attacks, indicating a steady level of activity.
- Hunters International registers 3.40%, signaling its emergence in the ransomware ecosystem.
- Qilin maintains a 3.24% share of total attacks.
- BlackSuit rounds out the list with 3.09%, remaining a consistent, though smaller, threat.
Emerging Ransomware Variants and Tactics
- 2025 has seen the debut of over 94 unique ransomware strains, including ShutterLock, NebulaCrypt, and PulseHive.
- Fileless ransomware attacks now make up 12% of infections in 2025, bypassing traditional signature-based detection.
- Ransomware with worm-like behavior, capable of spreading laterally, has been identified in 19% of corporate incidents in 2025.
- A new trend in “slow encryption” tactics, designed to evade real-time alerting, appears in 14% of new variants in 2025.
- Browser-based ransomware payloads, spread via extensions, have been detected in 1.2% of ransomware cases in 2025.
- The use of fake software updates to deliver ransomware has spiked 39% this year, targeting both Windows and MacOS.
- Double extortion models remain prevalent, with 81% of ransomware strains now exfiltrating data before encryption in 2025.
- AI-driven evasion logic is embedded in 7% of all ransomware binaries seen in 2025, adjusting behavior based on endpoint defenses.
- Fake job application payloads continue to exploit HR departments, with a 26% success rate among SMEs in 2025.
- Ransomware now includes geo-fencing logic in 5.3% of cases, refusing to execute in countries like Russia, Belarus, or Iran.
Trends in Cyber Insurance Claims Related to Ransomware
- Ransomware claims accounted for 52% of all cyber insurance payouts in 2025.
- The average ransomware claim in 2025 is $1.72 million, driven by extended downtime and legal recovery costs.
- Coverage exclusions for ransom payments were cited in 37% of denied claims in 2025.
- Premiums for high-risk industries (like healthcare and legal) have risen 31% on average in 2025.
- Insurers now require proof of endpoint detection, immutable backups, and MFA implementation in 93% of active cyber policies in 2025.
- Average policy deductibles for ransomware claims rose to $290,000 in 2025, a 19% year-over-year increase.
- 47% of covered businesses reported partial payout disputes due to ambiguous contract terms in 2025.
- Pre-breach assessments are now mandatory for policy renewal with 78% of major insurers as of 2025.
- Reinsurers are placing caps on ransomware-related coverage, limiting some organizations to $2 million per event.
- 35% of insured companies** report that cyber coverage influenced their ransomware incident response decision-making in 2025.
Recent Developments in Ransomware Prevention Technologies
- In 2025, endpoint detection and response (EDR) tools with AI behavior modeling now detect 89% of known ransomware strains in test labs.
- Zero-trust architecture adoption grew by 54% across US enterprise networks in the first half of 2025.
- Decryption-as-a-service tools, developed in collaboration with Europol, helped unlock files in 12% of ransomware cases without payment in 2025.
- DNS-layer security tools blocked an estimated 18 billion ransomware command-and-control (C2) requests in Q1 2025 alone.
- Immutable storage snapshots are now a feature in 61% of enterprise cloud platforms as of mid-2025.
- Email security platforms using natural language processing (NLP) models reduced phishing-triggered ransomware by 37% in 2025.
- USB port control software blocked 5.2 million malicious payloads across government devices globally in 2025.
- SIEM and SOAR platforms reduced the average ransomware incident response time by 42% in 2025.
- Threat intelligence-sharing alliances across industries expanded to include 4,000+ organizations globally in 2025.
- Ransomware honeypot systems detected 27,000 unique payload variations between January and May 2025 alone.
Conclusion
Ransomware in 2025 is no longer just a security issue; it’s a strategic risk that touches nearly every facet of modern business. As ransomware-as-a-service continues to commoditize attacks, and AI-enhanced tactics shorten detection windows, even well-defended organizations face pressure. Yet, the data also points to progress: faster response times, better prevention tools, and a growing shift in behavior from paying ransoms to refusing them.
The numbers tell a compelling story, one of escalating threats, evolving responses, and an arms race between defenders and adversaries. The question is no longer if you’ll be targeted, but how ready you’ll be when it happens.


































































