WHAT WE HAVE ON THIS PAGE
- Editor’s Choice
- Source Countries Behind Cyber Attacks
- Global Volume of Phishing Emails
- Email Spoofing and Brand Impersonation Rates
- Types of Phishing Involved in Major Security Incidents
- Success Rates of Phishing Campaigns
- Phishing Email Detection and Filtering Effectiveness
- Phishing Demographics by Age Group
- Financial Impact of Phishing Attacks
- Role of AI and Automation in Phishing Campaigns
- Different Types of Spam Emails
- Phishing Trends in Business Email Compromise (BEC)
- Employee Click-Through and Engagement Rates
- Industries Most Targeted by Phishing Emails (Malicious Emails per Worker per Year)
- Common Subject Lines and Triggers Used in Phishing Emails
- Types of Data Most Commonly Compromised
- Recent Developments in Phishing Email Tactics
- Conclusion
- Sources
It started like any other Tuesday morning. A mid-level finance manager at a US-based logistics firm opened what looked like an urgent request from their CEO. The subject line? “Quarterly Financial Review Needed Immediately.” The logo looked legit. The tone felt familiar. Within two minutes, confidential files were shared, and by noon, the company had lost $1.2 million to a meticulously crafted phishing attack.
This isn’t just an isolated mistake—it’s part of a rapidly growing global threat. In 2025, phishing emails remain one of the most persistent and successful cyberattack vectors, evolving with smarter lures, AI-generated content, and increasingly deceptive visuals. Whether you’re a small business owner or a global enterprise executive, these stats offer critical insights into the scale, trends, and risks of phishing emails in 2025.
Editor’s Choice
- Over 3.4 billion phishing emails are sent per day in 2025.
- 73% of organizations globally reported at least one successful phishing attempt this year.
- Business Email Compromise (BEC) scams via phishing now cost the average US business $187,000 per incident.
- 47% of phishing emails in 2025 successfully bypass standard email security filters.
- Financial institutions remain the most impersonated sector, accounting for 33% of all phishing attempts.
- The click-through rate on phishing emails that use urgency triggers (e.g., “Update your credentials”) has hit 18% in 2025.
- Nearly 1 in 4 phishing attacks now use AI-generated language to improve personalization and believability.
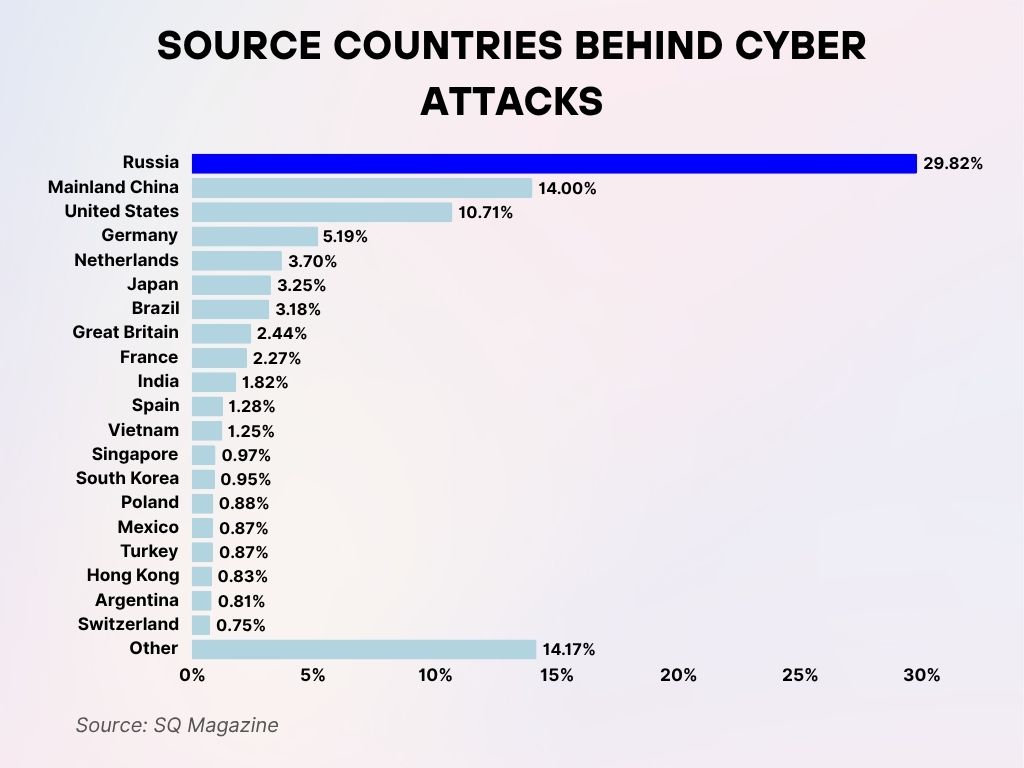
Source Countries Behind Cyber Attacks
- Russia is the largest source of cyber attacks, accounting for a staggering 29.82% of all incidents.
- Mainland China ranks second, responsible for 14.00% of attacks globally.
- The United States comes third, contributing 10.71% to the total.
- Germany is next with 5.19%, followed by the Netherlands at 3.70%.
- Japan and Brazil show nearly equal threat levels at 3.25% and 3.18%, respectively.
- Great Britain makes up 2.44% of attack sources, with France closely behind at 2.27%.
- India accounts for 1.82%, indicating growing global involvement.
- Other notable contributors include Spain (1.28%), Vietnam (1.25%), Singapore (0.97%), and South Korea (0.95%).
- Countries like Poland, Mexico, Turkey, Hong Kong, and Argentina each fall under 1%, but still play a role in global cyber activity.
- Switzerland has the smallest identified share at 0.75%.
- Attacks from unidentified or other regions constitute a significant 14.17% of the total.
Global Volume of Phishing Emails
- As of Q2 2025, an estimated 102 billion phishing emails have been circulated globally, marking a 22% year-over-year growth.
- North America accounts for 38% of global phishing email volume, followed by Europe at 27% and Asia-Pacific at 21%.
- Cloud-based work environments have seen phishing volumes increase by 30% compared to hybrid or on-premise setups.
- Government institutions across 18 countries reported a 42% increase in phishing attempts aimed at critical infrastructure in early 2025.
- Phishing-as-a-Service (PhaaS) platforms on the dark web have grown by 49%, making phishing more accessible to low-skill threat actors.
- Healthcare organizations reported a 35% spike in phishing volumes in Q1 2025, especially those handling patient scheduling or billing.
- During global events or crises (e.g., elections, economic updates), phishing email surges can spike by as much as 68% in affected regions.
- Mobile device users now receive nearly 28% of all phishing emails.
- The average phishing email campaign now lasts 96 hours before detection and shutdown.
- Globally, spam filters have identified an average of 29 phishing attempts per user per month in 2025.
Email Spoofing and Brand Impersonation Rates
- Microsoft, Amazon, and Google are the top three most impersonated brands in phishing emails this year.
- In 2025, 72% of phishing attacks involved some form of brand spoofing.
- Spoofed email domains now bypass SPF and DKIM protocols in 11% of all phishing messages.
- Brand impersonation emails with visual logos and real signatures increased engagement rates by 19% over plain-text attacks.
- The financial services sector saw a 32% increase in phishing emails spoofing internal communication tools like Slack and Microsoft Teams.
- Domain shadowing—the use of subdomains on legitimate sites for phishing has surged by 43% year-over-year.
- About 14% of phishing emails now spoof legitimate CRM platforms like Salesforce to steal login credentials.
- Social media impersonation emails targeting LinkedIn users rose by 56% in the first half of 2025.
- Government agency impersonation has also spiked, with the IRS and DMV among the most spoofed institutions during tax season.
- AI-driven phishing kits are now capable of cloning entire landing pages, reducing detection likelihood and improving credential capture rates by 23%.
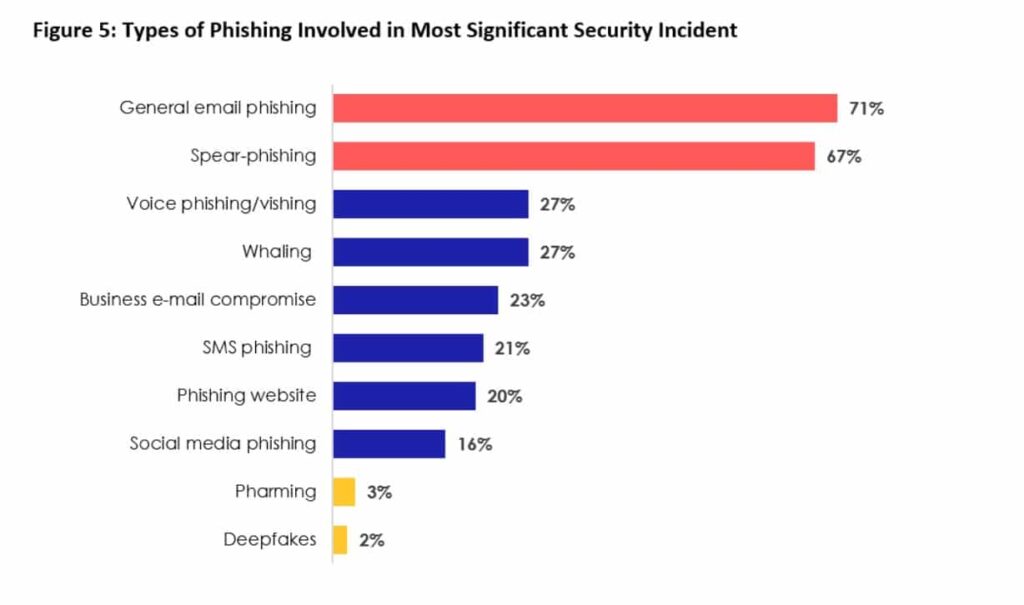
Types of Phishing Involved in Major Security Incidents
- General email phishing is the most common, involved in 71% of major security breaches.
- Spear-phishing follows closely behind at 67%, targeting specific individuals or organizations.
- Voice phishing (vishing) and whaling each contribute to 27% of incidents.
- Business email compromise (BEC) was involved in 23% of reported attacks.
- SMS phishing (smishing) accounted for 21%, showing the growing mobile threat.
- Phishing websites were linked to 20% of incidents, often used to steal credentials.
- Social media phishing played a role in 16% of security breaches.
- Pharming and deepfakes, though less common, were still involved in 3% and 2% of incidents, respectively.
Success Rates of Phishing Campaigns
- In 2025, the overall success rate of phishing campaigns has reached 9.4%.
- Campaigns that use deepfake audio and AI-generated sender voices in follow-up calls have a 24% higher success rate than text-only emails.
- Spear-phishing emails, customized for high-value targets, now see success rates above 39%, especially within executive-level inboxes.
- The use of QR code phishing (Quishing) has exploded in 2025, increasing success rates by 62% due to lower user awareness.
- Multi-layered phishing campaigns, which combine emails with SMS or voice phishing (vishing), are twice as effective as single-channel approaches.
- Credential-harvesting emails succeeded in 14% of attacks that mimicked common SaaS platforms like Zoom or Microsoft 365.
- Real-time phishing sites now stay live for an average of 5 hours longer before takedown, giving attackers more opportunity to exploit victims.
- Educational institutions reported a 17% success rate for phishing campaigns, due to more relaxed BYOD security policies among faculty and students.
- Follow-up phishing (where attackers respond to their own phishing email to continue the conversation) increased success likelihood by 28%.
- Victims who interacted with a phishing email once were 32% more likely to fall for a second attack within the same year.
Phishing Email Detection and Filtering Effectiveness
- As of mid-2025, email security filters block about 81% of phishing emails on average, due to more sophisticated techniques.
- AI-powered email filters using natural language processing are now 36% more effective than traditional rule-based filters.
- Cloud-based email platforms (like Google Workspace and Microsoft 365) report detection rates of 92% for phishing attempts.
- Despite advancements, 47% of phishing emails still bypass basic spam detection, especially those using obfuscated links or image-based payloads.
- Zero-day phishing emails, or those using never-before-seen tactics, evade detection in 1 out of 5 attempts.
- Filters that use sender reputation scores now falsely flag 4.1% of legitimate emails, raising concerns over email delivery integrity.
- Behavioral analysis tools, which examine recipient interaction patterns, have helped reduce phishing email success by 19% in organizations using them.
- A new detection layer using machine vision to analyze embedded logos and design patterns caught 34% more phishing attempts than legacy systems.
- Employee feedback loops, where users report suspicious emails, now contribute to 22% of detection improvements across enterprise platforms.
- Dark web data-sharing on phishing campaign signatures has improved global filter response time by 12 hours on average.
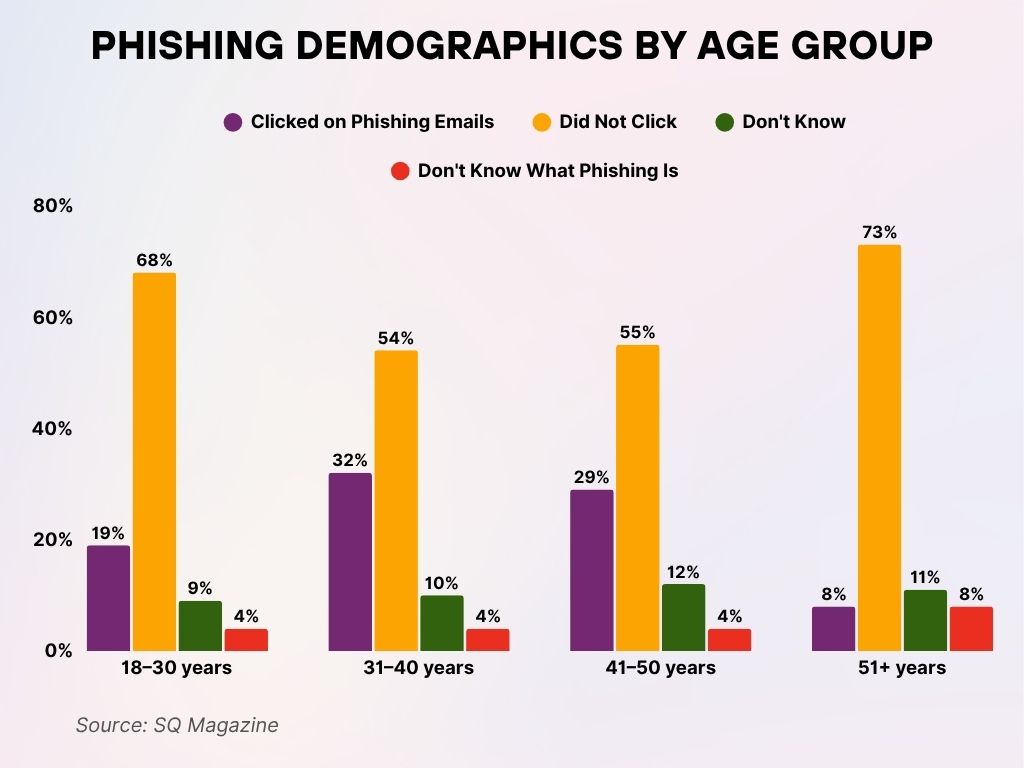
Phishing Demographics by Age Group
- 18–30 years: Among younger adults, 19% admitted to clicking on phishing emails, while 68% successfully avoided them. 9% were unsure whether they had clicked, and 4% didn’t even know what a phishing email is, highlighting a small but notable awareness gap.
- 31–40 years: This group had the highest click rate at 32%, showing a greater vulnerability. 54% managed to avoid phishing emails, 10% were uncertain, and 4% were unaware of what phishing actually is, suggesting room for more cybersecurity education.
- 41–50 years: In this middle-aged group, 29% clicked on phishing emails, while 55% avoided them. 12% didn’t know if they had clicked, and 4% lacked basic awareness of phishing emails, similar to younger groups.
- 51+ years: Older adults were the most cautious, with only 8% clicking on phishing emails and 73% avoiding them, the highest non-click rate of all age groups. However, 11% were unsure, and 8% admitted they don’t know what a phishing email is, the largest knowledge gap across all groups.
Financial Impact of Phishing Attacks
- In 2025, the average cost of a phishing attack in the US has climbed to $4.17 million, compared to $3.86 million last year.
- Small and mid-sized businesses (SMBs) are disproportionately affected, suffering an average loss of $328,000 per incident.
- For enterprises, downtime caused by phishing-related breaches now costs $9,500 per minute.
- Credential theft phishing attacks have contributed to 43% of all data breach costs in 2025.
- Phishing-related fraud accounted for $6.8 billion in global business losses in the first half of 2025 alone.
- Industries most affected financially include healthcare, finance, and SaaS, with an average loss per breach of $5.1 million.
- Recovery time for phishing attacks now averages 22 days, with a further 17 days for full operational resumption in sensitive industries.
- Cyber insurance premiums have risen by 21% in 2025, largely driven by phishing claims.
- Companies without phishing training programs are 3.5x more likely to incur losses exceeding $500,000.
- Legal settlements and regulatory fines related to phishing breaches have totaled $850 million globally in just the first two quarters of 2025.
Role of AI and Automation in Phishing Campaigns
- In 2025, AI-generated phishing emails account for nearly 32% of all phishing activity.
- Generative AI tools are now used to automatically customize phishing messages using scraped social media and dark web data.
- Some phishing campaigns are capable of auto-rewriting subject lines and body copy to evade detection in real-time.
- Chatbots trained on stolen email histories are being used in spear-phishing to mimic real employees’ writing styles.
- Language models now generate phishing content in 10+ languages, enabling multilingual phishing attacks targeting global businesses.
- Attackers deploy phishing bots to monitor login pages and send alerts when credentials are captured, cutting human effort by 70%.
- Phishing kits powered by AI can now replicate entire websites with functional login forms in under 5 seconds.
- Deepfake tools are integrated into BEC scams, generating synthetic audio or video messages for more believable executive impersonation.
- Automated targeting systems scrape LinkedIn, CRM databases, and resume sites to build hyper-targeted recipient lists at scale.
- AI-enhanced phishing attacks are 42% more likely to pass through basic defenses due to their syntactic complexity and human-like tone.
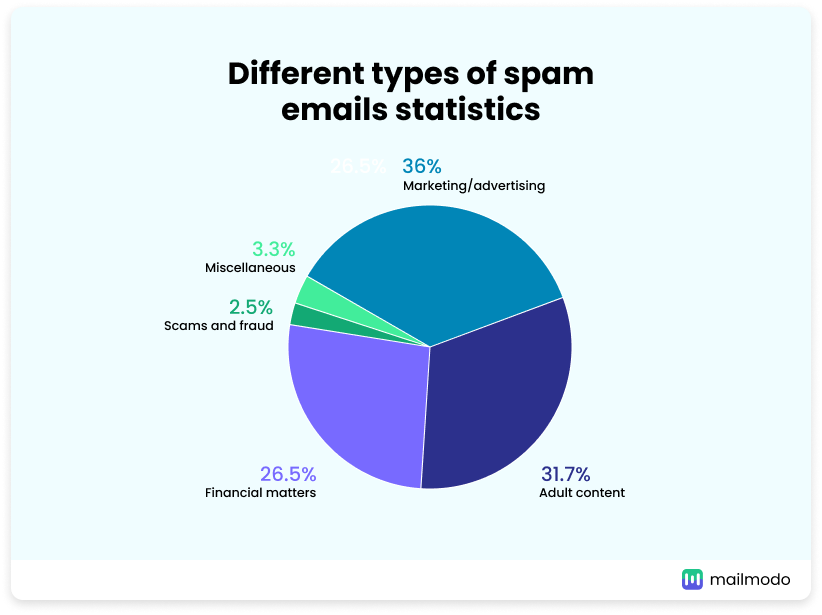
Different Types of Spam Emails
- Marketing/advertising emails make up the largest share of spam at 36%, flooding inboxes with promotions and deals.
- Adult content accounts for 31.7% of all spam emails, making it the second most prevalent type.
- Financial matters, including loans and investment offers, represent 26.5% of spam volume.
- Scams and fraud make up 2.5%, posing serious threats through deceitful tactics.
- Miscellaneous spam emails make up the remaining 3.3%, covering various unclassified types.
Phishing Trends in Business Email Compromise (BEC)
- In 2025, BEC phishing scams now account for 28% of all phishing-related financial losses.
- The average BEC attack led to a direct financial loss of $187,000 per business, making it the costliest form of email fraud this year.
- Vendor impersonation has become the fastest-growing BEC vector, increasing by 41% year-over-year.
- Nearly 61% of BEC attacks now involve compromised employee credentials, making internal email chains a primary attack route.
- Reply-chain phishing, where attackers hijack existing conversations, rose 36% in the past year and is 3x more successful than cold-message BEC attempts.
- Payroll diversion scams, where attackers reroute employee salaries, have grown by 22%, especially in the education and healthcare sectors.
- BEC attacks impersonating CEOs or CFOs now make up 47% of all executive-targeted email threats.
- QR code usage in BEC emails has risen sharply, allowing attackers to bypass traditional link filters.
- Law firms and accounting agencies are the newest hotbeds for BEC phishing, with a 29% spike in reported incidents in Q1 2025.
- Companies with over 1,000 employees were twice as likely to experience a BEC attack compared to smaller firms.
Employee Click-Through and Engagement Rates
- In 2025, the average employee click-through rate on phishing emails is 11.6%.
- Phishing emails using emotionally urgent subject lines (e.g., “Account Suspended” or “Bonus Confirmation”) had a click rate of 21%.
- Employees under the age of 30 were 34% more likely to click on a phishing link than their over-50 counterparts.
- The retail sector continues to lead with the highest click rate at 15.3%, due to high turnover and seasonal workers.
- Training fatigue has set in at large enterprises—employees exposed to monthly simulations showed less responsiveness than those trained quarterly.
- Click rates for fake internal memos or policy update emails increased by 19%, indicating blind trust in internal branding.
- Remote workers are twice as likely to engage with phishing emails, particularly those spoofing productivity tools.
- The addition of company branding in phishing emails raised the click-through rate by 11.5%.
- Mobile users now account for over 30% of all phishing link clicks, reflecting increased workplace mobility and device crossover.
- Companies that implemented gamified training modules saw a 48% reduction in employee click rates after three months.
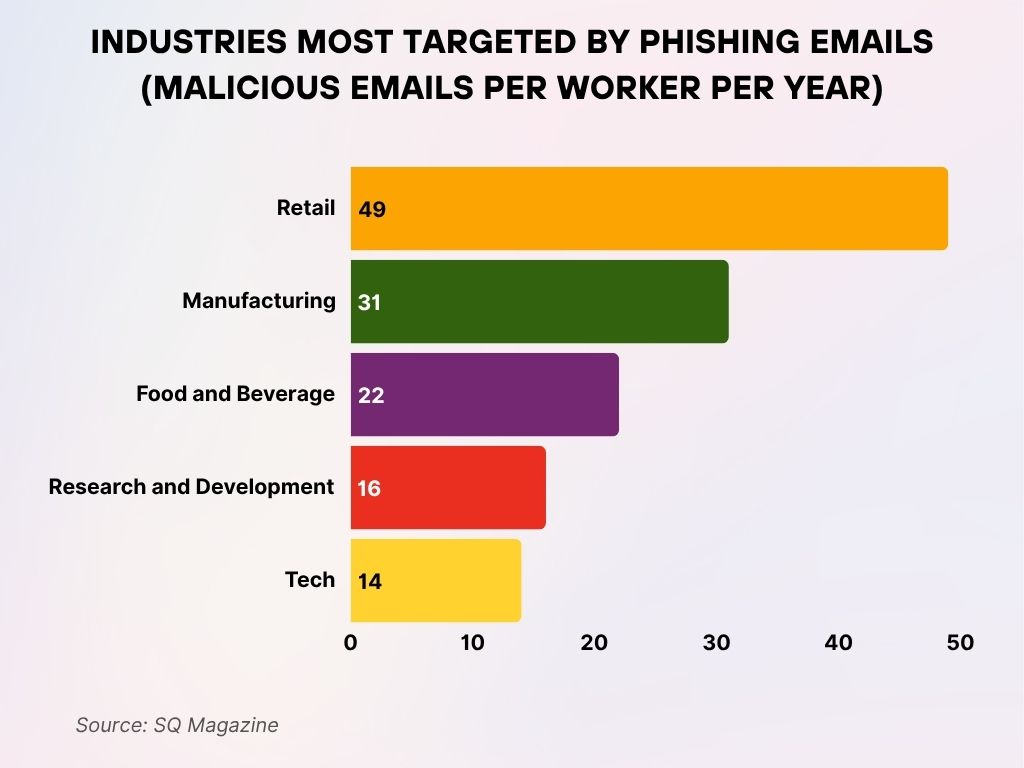
Industries Most Targeted by Phishing Emails (Malicious Emails per Worker per Year)
- The retail industry is hit hardest, with an average of 49 malicious emails per worker annually.
- Manufacturing follows, with each employee receiving about 31 phishing emails per year.
- The food and beverage industry faces 22 malicious emails per worker yearly.
- In research and development, workers receive 16 phishing emails per year.
- Even in the tech industry, employees get an average of 14 malicious emails annually.
Common Subject Lines and Triggers Used in Phishing Emails
- In 2025, the most effective phishing subject line remains: “Password Expiring Today – Immediate Action Required”, with a 26% open rate.
- “Unusual Login Attempt Detected” and “Your Invoice Is Ready” continue to lead in financial and IT-related phishing lures.
- 70% of phishing emails in 2025 use subject lines that mimic system-generated notifications (e.g., Outlook, Salesforce).
- Subject lines framed as HR updates (e.g., “Policy Change Notification” or “Annual Review”) yielded click-through rates of 18–22%.
- COVID-themed lures have dropped sharply but still appear in 0.7% of phishing messages, mostly in health sector environments.
- Seasonal phishing emails, especially around tax season, holidays, or payroll updates, spike up to 40% higher than normal volumes.
- Subject lines with “Re:” or “Fwd:” tags had a 17% higher open rate, exploiting familiarity bias.
- Trigger phrases like “Verify your identity” and “Account flagged for suspicious activity” were used in 33% of credential theft attacks.
- Attackers increasingly embed shortened URLs in subject lines to prompt curiosity and increase click-throughs.
- Emails imitating calendar invitations or meeting links rose by 25%, particularly in corporate environments using Google or Microsoft apps.
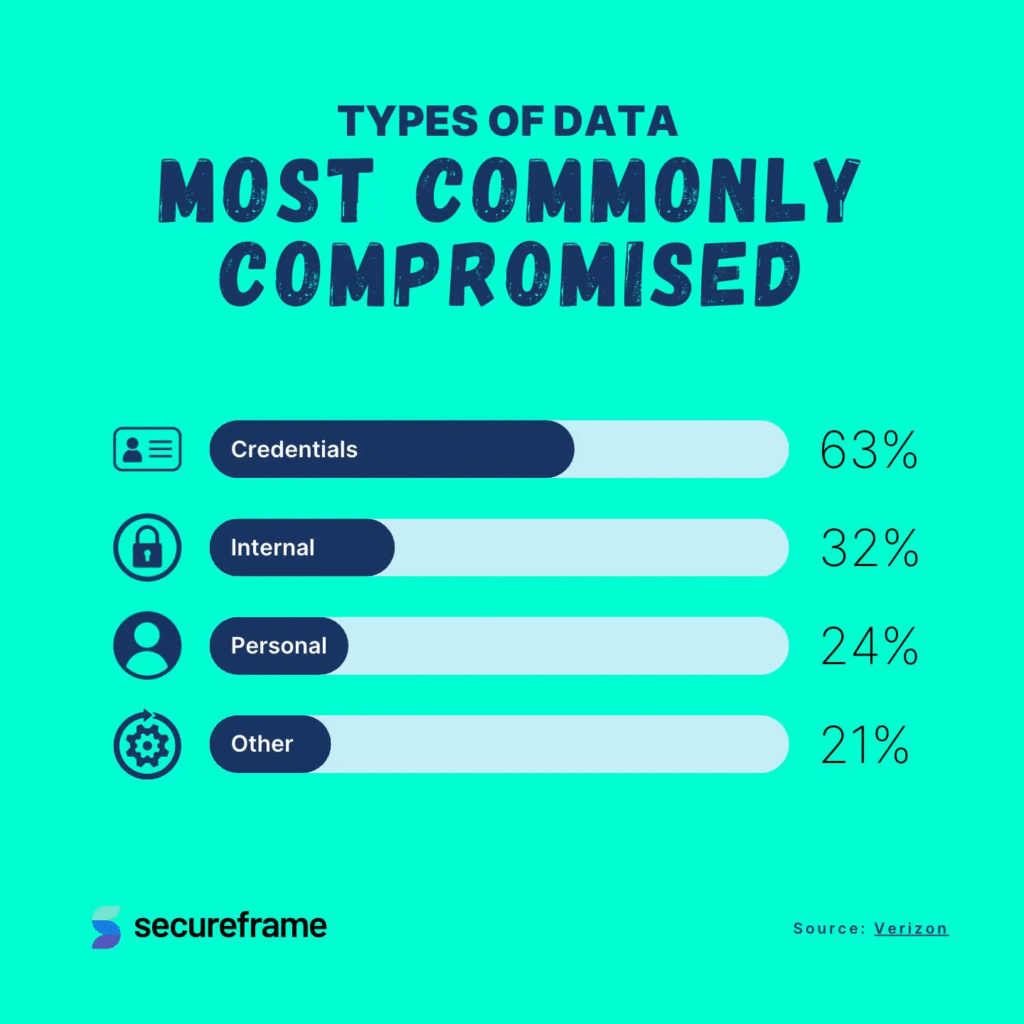
Types of Data Most Commonly Compromised
- Credentials are the most frequently targeted and compromised in 63% of breaches, exposing usernames, passwords, and login details.
- Internal data, such as confidential business information, is compromised in 32% of incidents.
- Personal information (like names, addresses, or contact details) is exposed in 24% of breaches.
- Other types of data, possibly including health, payment, or proprietary info, account for 21% of compromises.
Recent Developments in Phishing Email Tactics
- In 2025, image-based phishing emails (where text is embedded in images to evade scanners) increased by 48% from the previous year.
- HTML attachment phishing rose by 64%, leveraging legitimate-looking forms embedded in email attachments.
- Conversational phishing, where attackers engage over days or weeks before making malicious requests, is up by 31%.
- Synthetic identity phishing combines deepfake identities and AI-generated backstories, making scams 45% harder to detect.
- Time-delayed payloads, which activate malicious links hours after email delivery, evade 2025’s real-time scanning tools 32% more effectively.
- Phishing via collaboration tools (e.g., Slack, Teams, Notion) increased by 39%, as threat actors shift to new communication platforms.
- Attackers are using CAPTCHA-like email lures, where users must complete a fake human verification process, making the phishing flow seem more legitimate.
- ChatGPT-style spoof emails, written with high fluency and context awareness, have replaced broken English attacks of the past.
- URL evasion via redirects and web proxies has reached a new high, with 27% of malicious emails now using advanced obfuscation techniques.
- Phishing simulators used by attackers (not just defenders) help them fine-tune campaigns for maximum effectiveness.
Conclusion
Phishing in 2025 is no longer a crude, typo-laden attempt to fool the gullible. It’s a multi-layered, AI-powered assault on human behavior, business processes, and digital trust. With the rise of deepfakes, automation, and real-time adaptive content, today’s phishing emails are smarter, faster, and harder to detect than ever.
Every statistic tells a story of evolving tactics and shifting targets. But they also tell us where to focus: better training, adaptive technology, and proactive response. Whether you’re a solo entrepreneur or part of a multinational, staying ahead of phishing trends is no longer optional; it’s essential.
Sources
- https://www.coinbase.com/blog/consumer-protection-tuesday-check-your-email-headers
- https://thehackernews.com/2025/06/fake-recruiter-emails-target-cfos-using.html
- https://www.uow.edu.au/student/news/2025/phishing–did-you-take-the-bait-.php
- https://www.axios.com/2025/05/27/chatgpt-phishing-emails-scam-fraud
- https://www.statista.com/statistics/266155/number-of-phishing-attacks-worldwide/
- https://cybersecuritynews.com/phishing-attack-prevention/