A new wave of malware is hitting Windows systems hard, using fake shortcuts and USB drives to steal cryptocurrency and deploy more dangerous tools.
Quick Summary – TLDR:
- TinyLoader spreads through USB drives, fake desktop shortcuts, and network shares on Windows.
- It hijacks clipboard activity to steal Bitcoin, Ethereum, Litecoin, and TRON wallet addresses.
- The malware drops Redline Stealer and DCRat for deeper access and data theft.
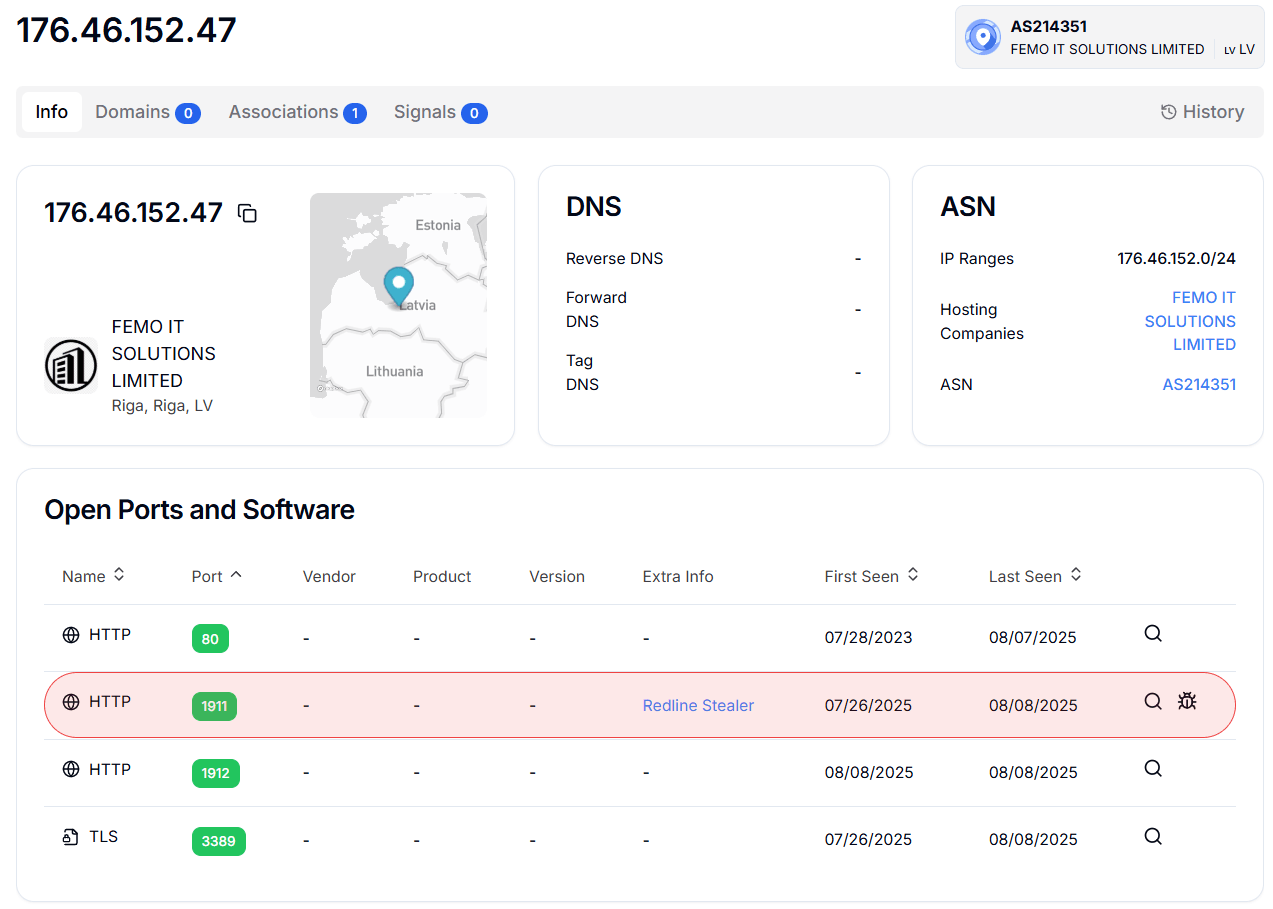
- Its command panels are hosted across Latvia, the UK, and the Netherlands, suggesting a global infrastructure.
What Happened?
Security researchers have uncovered a sophisticated malware campaign known as TinyLoader, targeting Windows users worldwide. The malware acts as both a stealthy cryptocurrency, data theft medium and a delivery platform for more malicious tools, spreading rapidly through common vectors like USB drives, fake shortcut files, and network shares.
🦠 𝗡𝗲𝘄 𝗥𝗲𝘀𝗲𝗮𝗿𝗰𝗵: 𝗙𝗿𝗼𝗺 𝗣𝗮𝗻𝗲𝗹 𝘁𝗼 𝗣𝗮𝘆𝗹𝗼𝗮𝗱 – 𝗜𝗻𝘀𝗶𝗱𝗲 𝘁𝗵𝗲 𝗧𝗶𝗻𝘆𝗟𝗼𝗮𝗱𝗲𝗿 𝗠𝗮𝗹𝘄𝗮𝗿𝗲 𝗢𝗽𝗲𝗿𝗮𝘁𝗶𝗼𝗻
— Hunt.io (@Huntio) September 2, 2025
TinyLoader is more than a loader.
It spreads through USB drives and shares, hijacks clipboard crypto addresses, and delivers Redline… pic.twitter.com/tejM8VAklZ
How TinyLoader Infects Windows Devices?
TinyLoader uses multiple attack methods to infect systems and persist undetected:
- USB Drives: It automatically copies itself with names like “Photo.jpg.exe” or “Document.pdf.exe” whenever a USB is connected. These files often include autorun scripts to launch on insertion.
- Fake Shortcuts: On desktops, it creates deceptive icons like “Documents Backup.lnk” with legitimate-looking descriptions to trick users into executing the malware.
- Network Shares: It scans local networks and copies itself to shared folders as “Update.exe” using system permissions, making it especially dangerous in office environments.
Once inside, TinyLoader creates hidden copies of itself in key directories and alters the Windows registry. If it gains admin rights, it hijacks file associations so that every time a .txt file is opened, the malware runs first.
Advanced Crypto Theft Through Clipboard Hijacking
The malware monitors the Windows clipboard in real time, checking four times per second. If a user copies a cryptocurrency wallet address, TinyLoader validates its format and silently swaps it with the attacker’s wallet address.
It targets:
- Bitcoin
- Ethereum
- Litecoin
- TRON
This tactic means users might send crypto to a criminal wallet without ever noticing.
Secondary Malware Deployment
TinyLoader also functions as a malware loader, reaching out to six attacker-controlled URLs to download additional payloads, including:
- Redline Stealer: Steals passwords, browser data, and wallet information.
- DCRat: A remote access trojan giving attackers full control over infected machines.
Once downloaded, these files (like “bot.exe” and “zx.exe”) are stored in the system’s temporary directory and executed immediately, turning the host into a multi-purpose attack platform.
Global Command and Control (C2) Network Uncovered
TinyLoader is backed by a distributed criminal infrastructure. Security teams traced it to:
- Two servers in Riga, Latvia
- One in London, UK
- One in Kerkrade, Netherlands
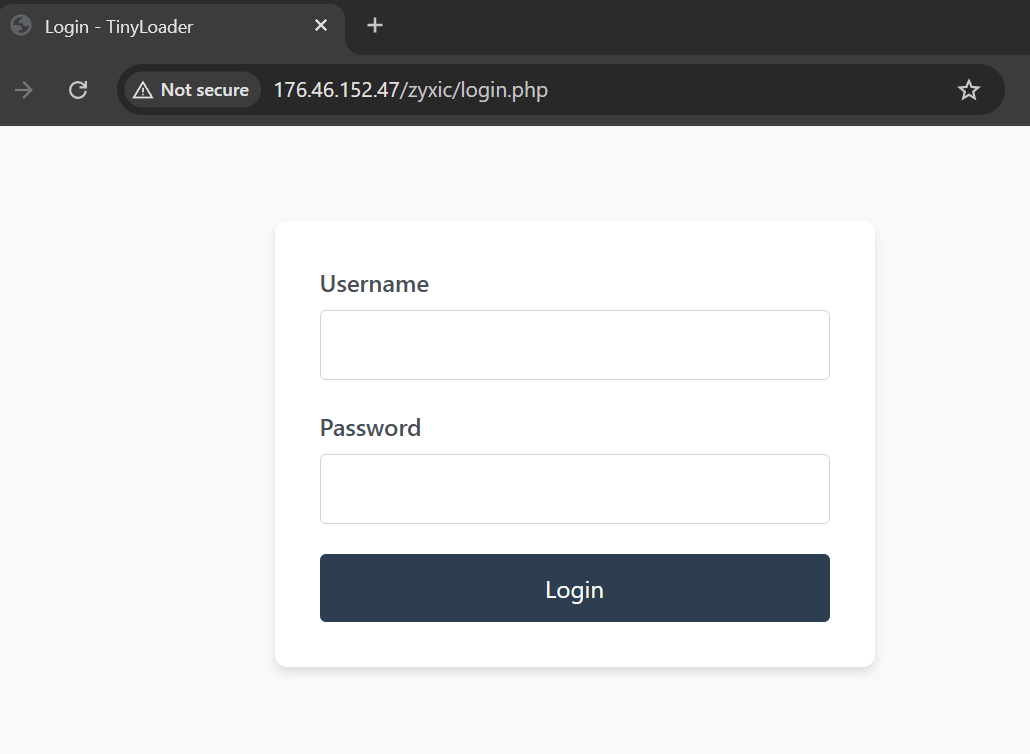
All are hosted by Virtualine Technologies, and one additional server is hosted by Railnet LLC in Great Britain. Each server operates a TinyLoader command panel, recognizable by the HTML signature: “Login – TinyLoader.”
Captured data confirmed these panels manage infected machines and coordinate the delivery of DCRat malware.
Indicators of Compromise (IOCs)
Malicious IPs:
- 176.46.152.47 – Riga, Latvia
- 176.46.152.46 – Riga, Latvia
- 107.150.0.155 – London, UK
- 77.90.153.62 – Kerkrade, NL
Malware Files:
- injector.exe.DcRat (98 KB) – Main payload injector
- c.exe.DcRat (49 KB) – Communication module
- svchost.exe.DcRat (65 KB) – Masquerades as Windows service
Defensive Strategies for Organizations and Users
To guard against TinyLoader:
- Block known IPs like 176.46.152.47 and monitor network traffic for the “Login – TinyLoader” signature.
- Restrict USB usage and scan all removable media.
- Audit network shares for unauthorized “Update.exe” files.
- Monitor for registry changes affecting file associations.
- Use endpoint detection tools that can catch high-frequency clipboard access.
For individual users:
- Always double-check wallet addresses before sending cryptocurrency.
- Be wary of shortcuts on your desktop claiming to be backup tools.
- Avoid opening files with double extensions like “.jpg.exe.”
SQ Magazine Takeaway
This malware is a perfect example of how cybercrime keeps evolving. It is not just one trick pony. TinyLoader spreads like a worm, steals your crypto with one copy-paste mistake, and opens the door to even more malware. What makes it really scary is how invisible it is. Everything looks normal while it is hijacking your wallet. As someone who follows security threats daily, I think this campaign is a wake-up call for both tech teams and average users. If you’re not watching clipboard activity or monitoring shared drives, you’re basically leaving the door wide open.


































































